Note: This is an additional lecture that is not part of any examination
IOT
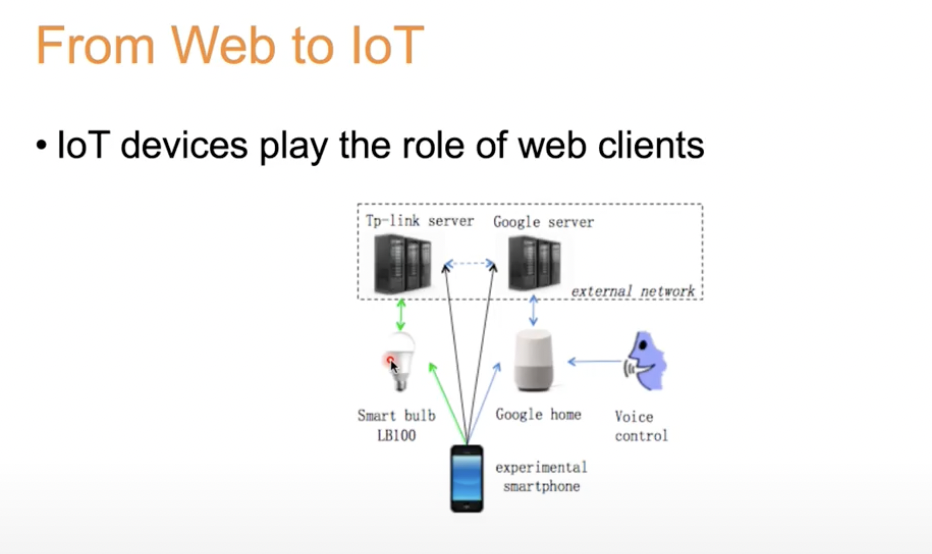 If looked at a different perceptive, we can see it such as the bulb acting as a web client. If the bulb acts like a web browser, we know that there is something we can extract from it like a token which could be used to access something.
If looked at a different perceptive, we can see it such as the bulb acting as a web client. If the bulb acts like a web browser, we know that there is something we can extract from it like a token which could be used to access something.
For google home, the AI part is just the voice recognition. Everything else is like a web browser. It is possible that we might even send our own voice to the web server.
Understanding the web would allow us to understand new system as they all make use of these concepts
New Techniques
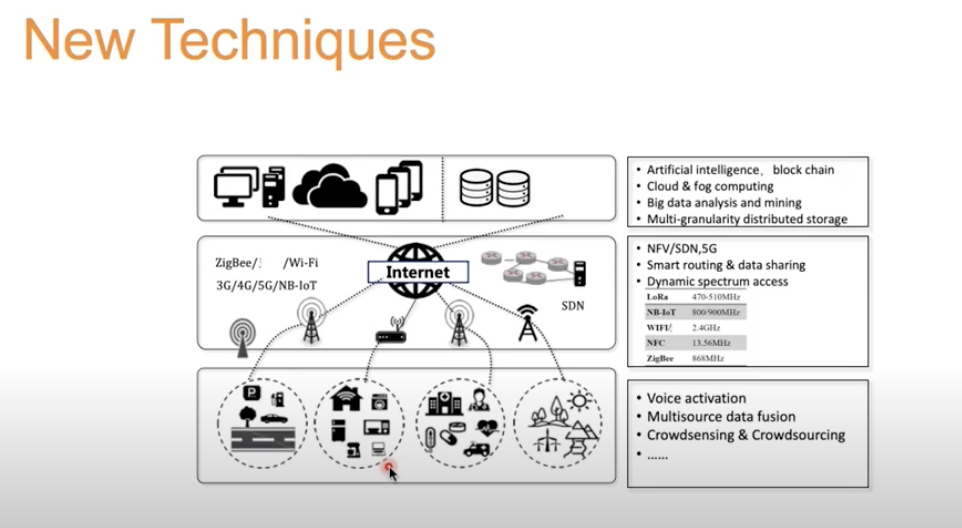
Everyone is trying to pretend to be a browser.
Device layers
- Hardware compromise, non-patch
- Signal Attack - Dolphin attacks
- Privacy Leakage
- Data transmission, Signal Level Side channel
- Hardware level side channel
The problem is that when a new technology is introduce, alot of companies just jump in. New technologies might be prone to vulnerabilities and this exposes these companies.
Signal attack: Prevent the signal from going to the device when detected. But this is hard to detect.
Tesla got their chips recycled and it seems like data is easily retrieved from these chips.
Signal Attack - Dolphin attacks
The ultra sound triggers some signal from the device. Some are not hearable by human but is pickable by machine.
Video at 13_1.mp4@22.17
There is no sound heard by human but is picked up by the machine. There is another attack where it uses laser beam from meteres away when hit the speakers, it can be recognised as voice.
In the room, if there is old style computer, our voice can actually change the hard disk.
Defence using Side-channel
Check the network traffic of a drone to detect whether it is watching you.
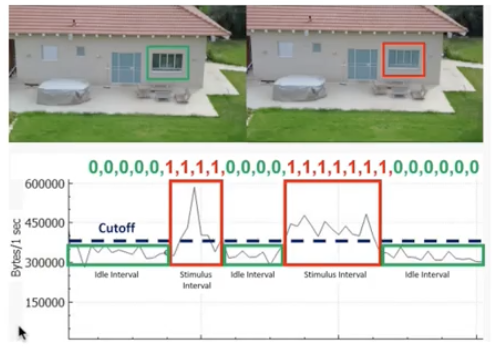
Zooming into the picture would cause an increase sending of data. This means that the traffic would increase. We can check this with wifi sniffers.
OTA Integrity
- Over the air updates
- Strictly checked on desktop OS and mobile phones
- e.g apple’s online validation of IOS version
- Much weaker checking in IoT devices
- Some vendor has no signature validation at all, over HTTP download
- Risk of firmware injection/replacement
IoT Security Problems - Network layer
- Heterogenerous network
- Traditional Network attacks
- e.g DDOS attack, utilize huge amounts of IoT devices - Maria
- New techniques always have two sides
- e.g SDN etc
- Data security - Non-encryption, side channel
Apple still pushes security patches even for the old devices. This is because its homogenous and could afford to update old devices. However, android only do this for the latest devices.
Apple might feel safer but because it is so homogenous, you can grab a iphone and find all the vulnerabilities (Since having a same version would mean the same across all iphone environment with the same version). However, compared to linux, due to the difference in environement variables, its hard to replicate the same system
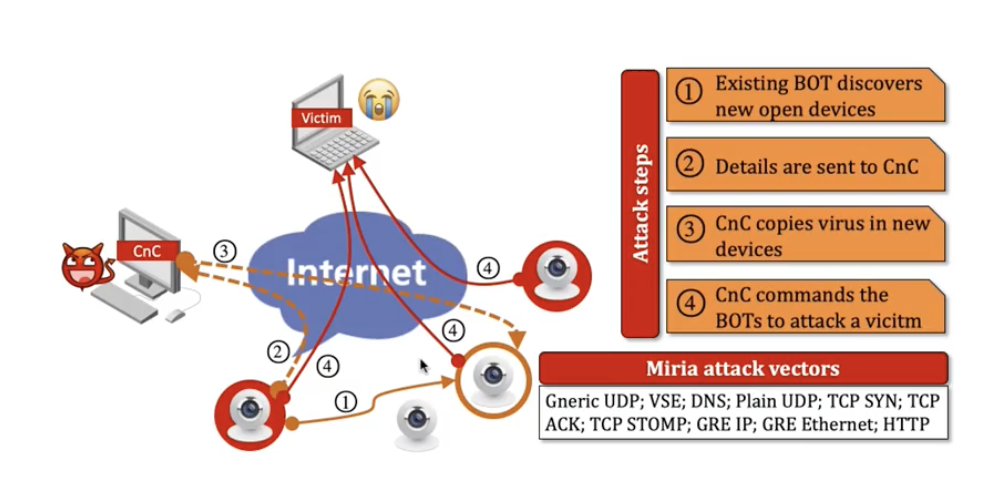
Mirai Attack
- Happen in 2016
- Use alot of IOT devices (Security camera) and is controlled by the attacker.
- The attacker makes use of this to cause a DDos within the DNS.
IoT Security Problems - Application layer
- Web security: Phishing, XSS, SQLi
- Cloud Security: Data integrity, confidentiality
- Android Security
- Least privilge
- Seperation of Privilege
- Malware
- Information leakage from Big DATA
- Security risk introduced by AI
- Access control - Over privilege problem
Summary
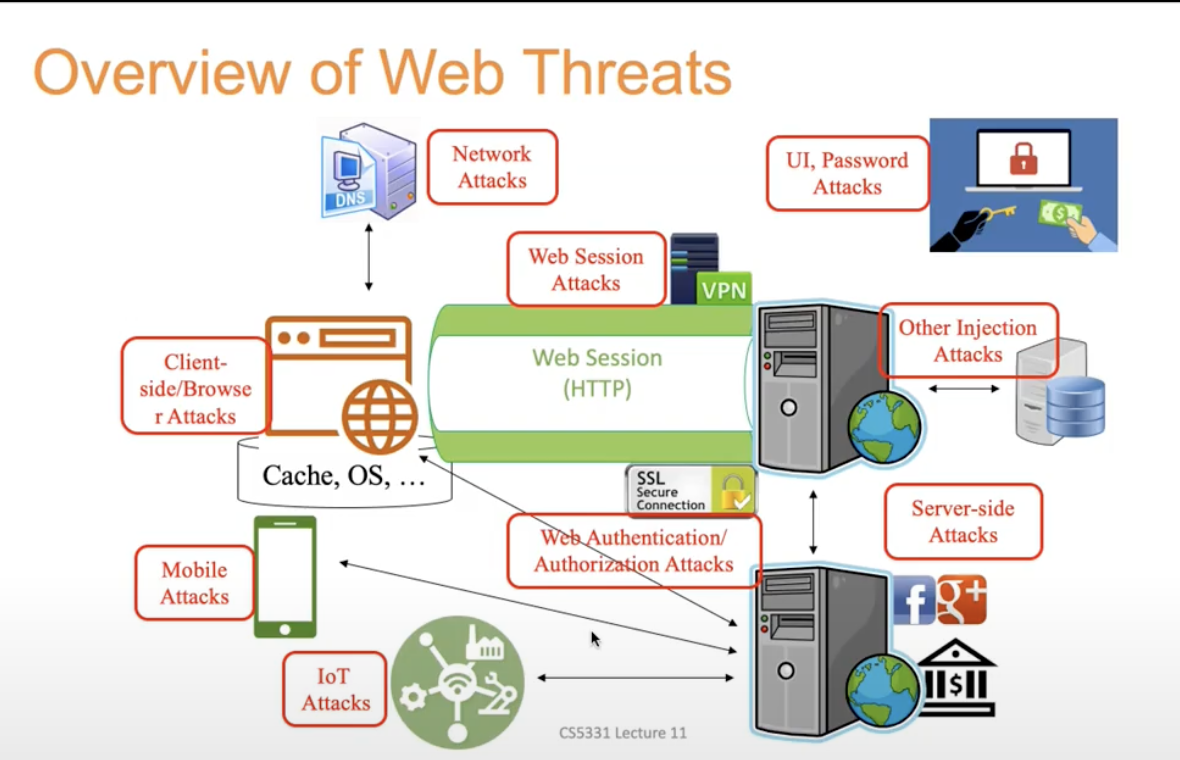
Simplification and concept
- Reach deep to the concept
- Illustrate concept using simplest examples possible
- Practice the task using simple tools
- Github webleaf
System Building is an Art or Business
- KISS (Keep it simple stupid)
- KICS (Keep it Complex and Smart) [Not good]