On lecture notes
Why does it happen
- Functionality: workability is always the first goal
- Security is the second goal
- Unawareness of security problems
- Unavoidable human mistakes
- awareness
- Lazy programmer: They don’t want to do checks
- Complex modern computing system
Functionality, Security and Trust
- Trust for functionality vs Trust for security
- you can trust someone for its function but it does not mean that you can trust the same person for security.
- E.g trusting CPU for computation vs for security enclave
Principle of Easiest Penetration
- Security is about every aspect of a computing system
- Hardware
- Software
- Data
- People
- Principal:
- Any system is most vuln at its weakest point
- Attackers do not follow rules
Why are they Web Objects
What ever api we use or protocol when accessing a web server, we pretend its a web browser. Even if its from your phone.
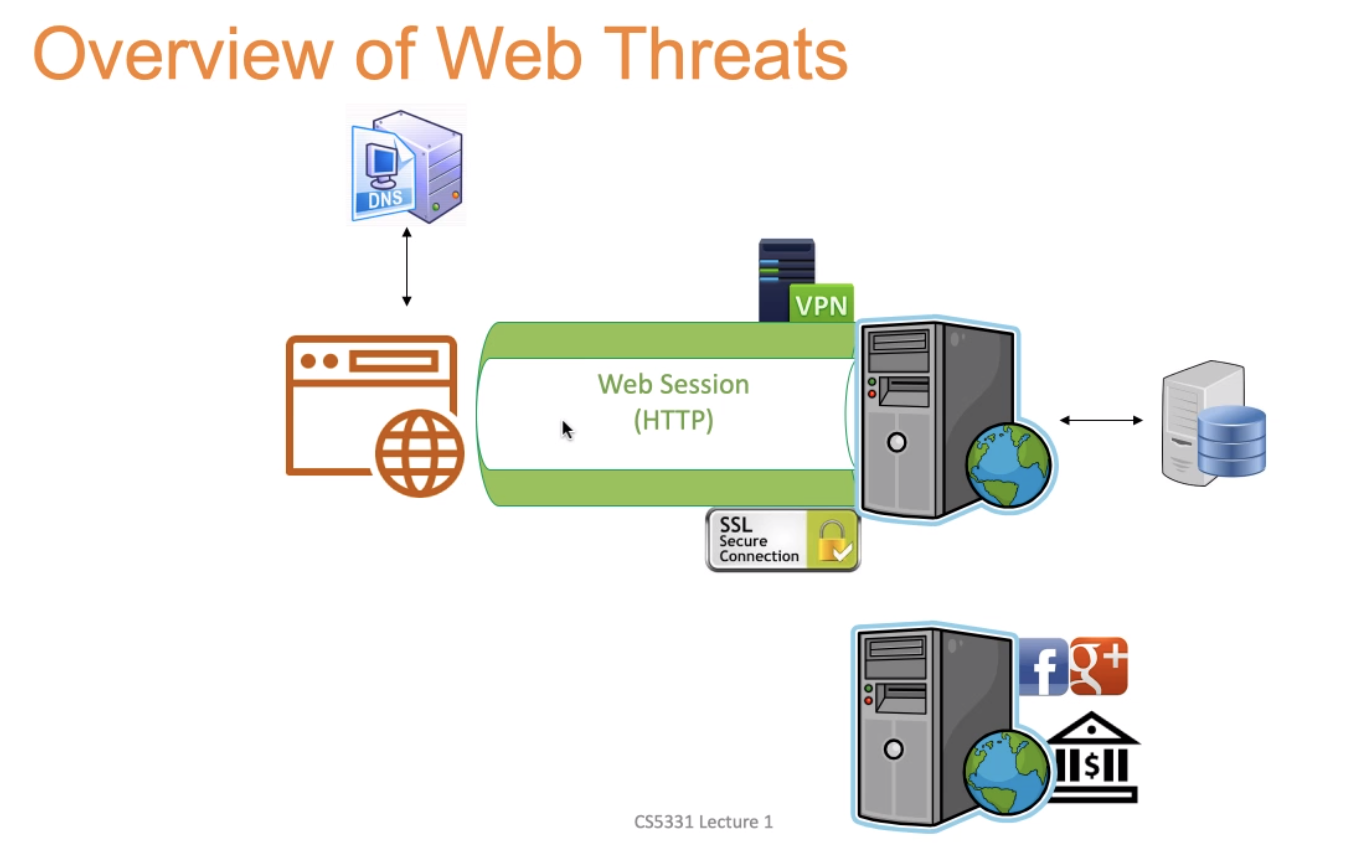
Overview of Web Threat
- People pretend to be browser
- DNS spoofing
- Web session (SSL Encryption): But the commands are still the same
- Sometime we have VPN
- IOT system
- Caching
- Password
- Phishing (human oriented attacks)
- Web authentication / Authorisation attacks
- Client-side / Browser attacks
Methodology
- How system work
- Attack - Break System
- How Attacks work
- Solution: New Defense
Undestand how the attack work and find a solution to this attack