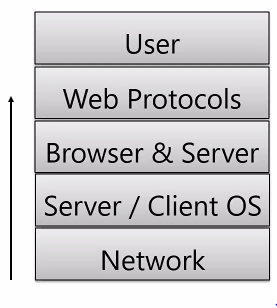
Possible attacks
- Database/server/cloud
- Insider gains unauthorised access
- Networking sniffing
- Bugs in the web app
- User impersonated
- Password Breach
Design computer systems with security in mind
Principles of secure Design
Go bottom up
- Threat Model
- Desired security property/goal
- Attacker capabilities
- Assumptions about the setup
Principal 1
Weakest Link Principal: Security can be no stronger than its weakest Link
Principal 2
Kerchkhoff’s principal: Security by Obscurity is bad
A good security is a security that does not base itself on obscurity. e.g IP protection