Useful links
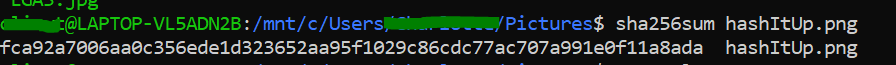
Hash it up
sha256sum hashItUp.png
Flag: flag{fca92a7006aa0c356ede1d323652aa95f1029c86cdc77ac707a991e0f11a8ada}
Decrypt me
- Just
openssl rsautl -decrypt -in flag.txt.enc -out decrypted.txt -inkey cs2107.pemFlag:flag{k33p_y0ur_pr1v473_k3y_2020deed}
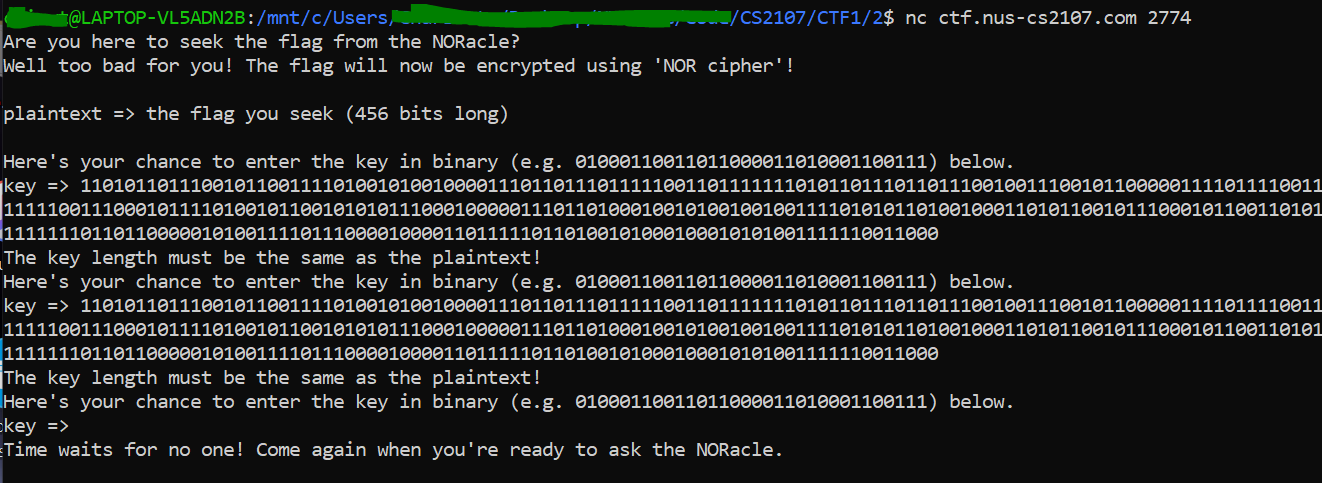
NORacle
- Asking to oracle:
- 256Character
Question:
000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
Ans:
100110011001001110011110100110001000010010011110110110111001010010100000101111101001000110111011101000001010011011001111110011111100111110001010100010101010000010001100101101111011111110110011100100111010000011000110110011001000101110100000110010001001011111001100101000001001100110010011101111101011100010100000101110011000110111001111100100101010000010001011101101111100110010100000100100011100111110001101101111101011110011001110100110101101111010000010
- Just not it to get the plaintext
- Plug in the binary string into some online binary to ascii converter: Link
Final flag: flag{a$k_AnD_Y000uu_sH@Ll_93t_7h3_flAG_Fr0m_tH3_n0rAC1e!}
This works because refer to the nor table.
Streaming
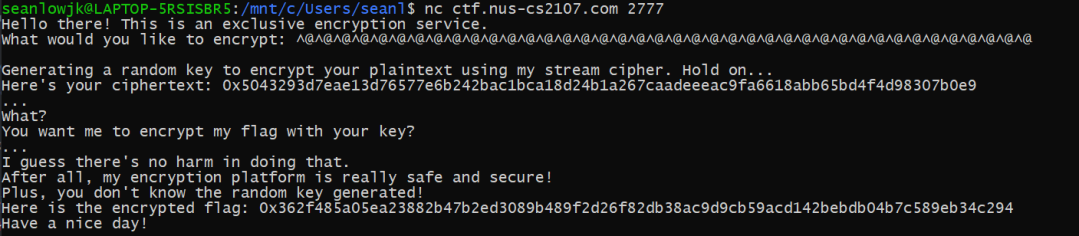
- Recieved ciphertext: 0x5043293d7eae13d76577e6b242bac1bca18d24b1a267caadeeeac9fa6618abb65bd4f4d98307b0e9 encrytped flag: 0x362f485a05ea23882b47b2ed3089b489f2d26f82db38ac9d9cb59acd142bebdb04b7c589eb34c294
Formula: k - key (Randomnised and hidden) A - My input (We have this) Return cipher text: (A xor k) Return Encripted: (F xor k)
Getting the Flag:
- Xor Ciphertext and Encrypted flag
- Xor the answer ciphertext
Reason:
- (A XOR K)(F XOR K) => This will cancel out the K which results in (A XOR F XOR 0)..
- Anything XOR 0 is itself, therefore we are left with (A XOR F)
- We can get F by Xoring the (A XOR F) with A since A will cancel out with each other
Flag: flag{D0_N0T_r3u5S_K3y_f0r_S7r3@m_c1Ph3r}
Brute force
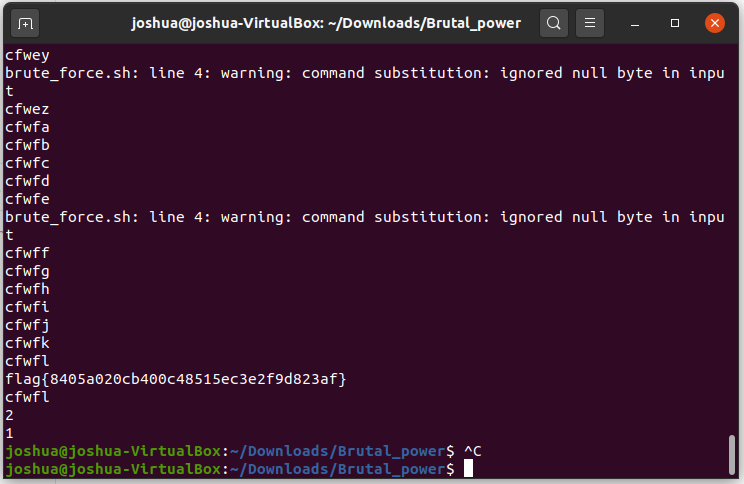
final flag: flag{8405a020cb400c48515ec3e2f9d823af}
Prohpet
Code used:
date_str2 = "2020-09-13 15:41:28"
date_dt2 = datetime.datetime.strptime(date_str2, '%Y-%m-%d %H:%M:%S')
print(get_epoch_seconds(date_dt2))
# Seed PRNG with current time
random.seed(get_epoch_seconds(date_dt2))
# Five attempts to guess my random number
fakeAnswer = int(random.random() * 133333333333337)
print("Fake answer: " + str(fakeAnswer))
- Just paste the time stamp string provided before
Flag: flag{R@nDoM_1s_n0t_r34lly_r4nd0m_Y3@H!}
Easy cook Book
- The first 16 characters entered will become the hash
- The recipe is stored in the `
/lookup/ - Hash is stored as the username in the cookie when the input is entered
- We will realised the file name is the hash for lookup
- Take the first 32 characters of the file name we want
tasty_flag_recipand take the first 32 characters in the hash - Take the remaining characters
e.txtand get the whole hash - Appending the two hash together and use it in the website as shown in 2)
Flag: flag{Gu3SS_1_MU3T_3t0P_Us1Ng_3C8!}
Hacker
- Decode cookie hacker:
console.log(decodeURIComponent("O%3A6%3A%22Hacker%22%3A2%3A%7Bs%3A17%3A%22%00Hacker%00show_flag%22%3Bb%3A0%3Bs%3A16%3A%22%00Hacker%00username%22%3Bs%3A10%3A%22hacker1337%22%3B%7D"))
This would yield the following json:
console.log(encodeURIComponent('O:6:"Hacker":2:{s:17:"Hackershow_flag";b:0;s:16:"Hackerusername";s:10:"hacker1337";}'))
- Encode cookie hacker:
console.log(encodeURIComponent('O:6:"Hacker":2:{s:17:"Hackershow_flag";b:1;s:16:"Hackerusername";s:10:"hacker1337";}'))
Notice how the b is change to 1 (This is because this field is the set_flag variable)
Download hash_extender: https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks
- Run code from hashing program:
./hash_extender --data O%3A6%3A%22Hacker%22%3A2%3A%7Bs%3A17%3A%22%00Hacker%00show_flag%22%3Bb%3A0%3Bs%3A16%3A%22%00Hacker%00username%22%3Bs%3A10%3A%22hacker1337%22%3B%7D --data-format html --signature 367f4643e26f0820db070629f43a5e6a614d778a5f1fd68d1fe1ce2d00b3934d --signature-format hex --append %20O%3A6%3A%22Hacker%22%3A2%3A%7Bs%3A17%3A%22%00Hacker%00show_flag%22%3Bb%3A1%3Bs%3A16%3A%22%00Hacker%00username%22%3Bs%3A10%3A%22hacker1337%22%3B%7D --append-format html --secret 32 --format sha256 --out-data-format html- Data: Original hacker cookie data encoded html string
- signature: Cookie encoded
- Appended data: New cookie (Encoded with flag = 1)
- Curl command:
curl -v --cookie "signature=d75231d2509f6612c149996756e35dbed961e6dbf5c428f74733b3715f49dce1; hackers=O%3a6%3a%22Hacker%22%3a2%3a%7bs%3a17%3a%22%00Hacker%00show%5fflag%22%3bb%3a0%3bs%3a16%3a%22%00Hacker%00username%22%3bs%3a10%3a%22hacker1337%22%3b%7d%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%03%c0+O%3a6%3a%22Hacker%22%3a2%3a%7bs%3a17%3a%22%00Hacker%00show%5fflag%22%3bb%3a1%3bs%3a16%3a%22%00Hacker%00username%22%3bs%3a10%3a%22hacker1337%22%3b%7d" http://ctf.nus-cs2107.com:2771
Flag: flag{Gr34t_woRk_h0Pe_Y0U_L3arNt_@_10t_Solv1ng_tHiS_cHalleNg3!}